I send a lot of abuse reports to hosts and registrars, but normally never receive any kind of response from +GoDaddy, sometimes they remove the fake site I'm reporting, sometimes they don't.
But this reply, eventually received is nonsensical at best.
"Dear Sir/Madam,
Thank you for contacting GoDaddy's Domain Name Abuse department.
Unfortunately we cannot assist with this issue through this department.
GoDaddy does not allow illegal content on our customer's websites. However, as a Registrar/Hosting provider, it is not our place to determine if the site you have mentioned is actually engaging in illegal activities. GoDaddy suggests reporting your issue to IC3 via their File a Complaint page. The Internet Crime Complaint Center (IC3) is a partnership between the Federal Bureau of Investigation (FBI) and the National White Collar Crime Center (NW3C) who accepts online Internet crime complaints filed by a person who believes they were defrauded.
GoDaddy regularly works with courts and law enforcement from the local to the international level and has a long-standing history of cooperation with these groups. Should we receive notification from these groups in regards to this issue we will be able to work with them on the matter.
Sincerely,
Domain Name Abuse
GoDaddy"
If it's not your place to determine whether sites you register and host are abusing your services in order to commit fraud, then how do you know you don't allow it?
Because GoDaddy apparently can't recognise a fake bank when they see one on their own servers.
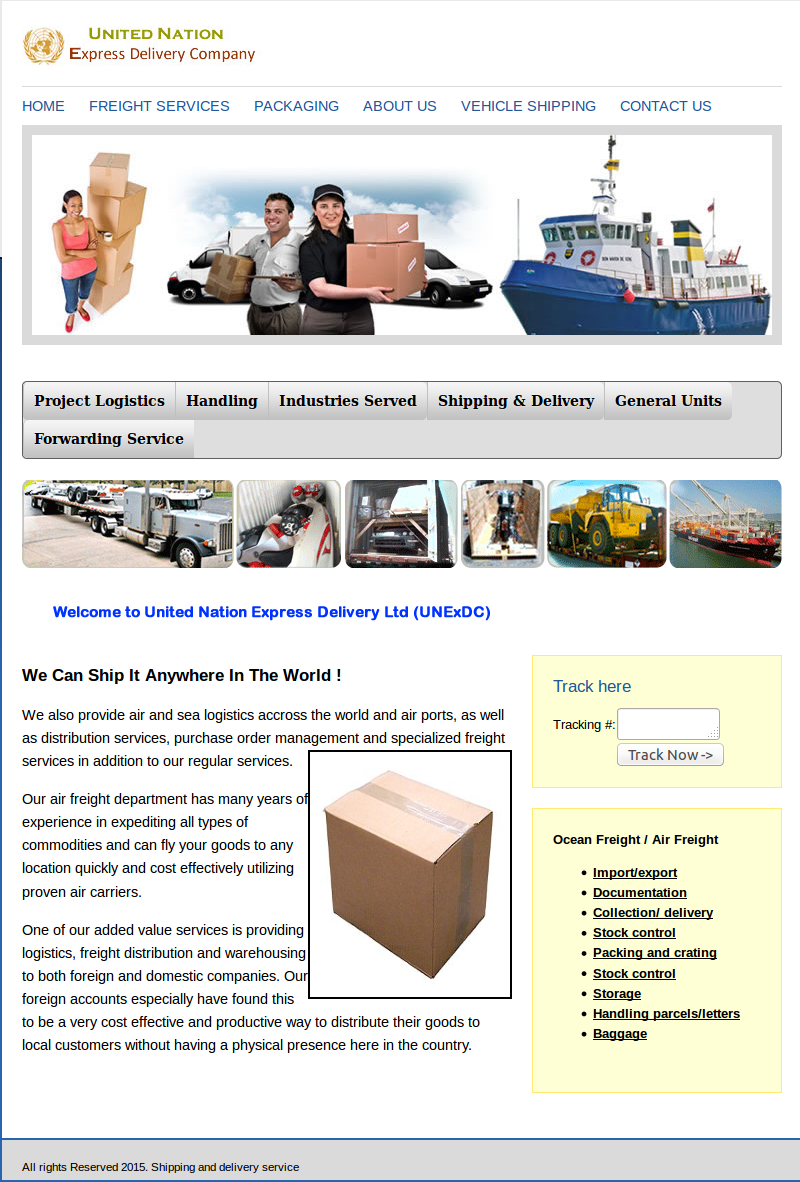
http://frdbk.com/
Or even two, because it has a clone at http://www.meshraqbank.com/.
What makes this a fake bank? Well, lets have a closer look and see.
It claims to be a bank in the UAE, but is not registered there according to the Emirates Central Bank.
On the home page we can see that while the logo is for FRD bank, in the text on the page it refers to itself as FGD bank! Which is it? Incidentally, FGD Bank isn't registered in the UAE either.
And here's the unsecured login page, shared by both sites:
http://frdbk.com/bank/index.php
And, if that wasn't enough, should you, and I would most definitely advise against it, still wish to register as a 'customer' of this fake bank here's the form.
http://frdbk.com/bank/registration.php
 |
| Everything needed to commit ID theft, on one unsecured page... |
Then how do they explain this site, registered with them and still remaining on their servers, after first being informed of it's abuse of their services in April?
http://milton-laboratories.com/
 |
| Black Money chemicals brought to you courtesy of GoDaddy |
Yes, it's another Black Money Chemical site registered and hosted with Godaddy.
Offering a range of weird and wonderful chemicals, all of which are guaranteed to 'solve' your Black Money problems!
Offering a range of weird and wonderful chemicals, all of which are guaranteed to 'solve' your Black Money problems!
The Black Money Scam is probably the most obvious of the 419 Advance Fee Fraud sites, but GoDaddy can't see the problem with this site either.
Fake banks, Black Money Chemical sites and others. GoDaddy allows it's customers to create and maintain fraudulent websites, despite it's claims to the contrary.
Fake banks, Black Money Chemical sites and others. GoDaddy allows it's customers to create and maintain fraudulent websites, despite it's claims to the contrary.